Welcome to the second installment in our series on transparency at the Microsoft Security Response Center (MSRC). In this ongoing discussion, we discuss our commitment to provide comprehensive vulnerability information to our customers.
At MSRC, our mission is to protect our customers, communities, and Microsoft, from current and emerging threats to security and privacy. In our previous blog post, we explored the root causes behind vulnerabilities documented with CWEs. This post discusses documenting a new class of vulnerabilities: Cloud Service CVEs.
The Common Vulnerabilities and Exposures (CVE) program is celebrating its 25th anniversary this year, and Microsoft has always been an active participant. Over time, the industry has changed significantly, with cloud-based services becoming increasingly integral to our daily lives. In the past, Cloud service providers (CSPs) refrained from disclosing information about vulnerabilities found and resolved in cloud services, unless customer action was required. The common understanding was that if the customer didn’t need to install updates then no additional information was necessary to help them stay secure. However, as the industry matures, we recognize the value of transparency. Therefore, we are now announcing that we will issue CVEs for critical cloud service vulnerabilities, regardless of whether customers need to install a patch or to take other actions to protect themselves.
As our industry matures and increasingly migrates to cloud-based services, we must be transparent about significant cybersecurity vulnerabilities that are found and fixed. By openly sharing information about vulnerabilities that are discovered and resolved, we enable Microsoft and our partners to learn and improve. This collaborative effort contributes to the safety and resilience of our critical infrastructure.
This commitment aligns with the goals of Microsoft’s Secure Future Initiative (SFI), which outlines our engineering priorities. These priorities include transforming software development, implementing new identity protections, and improving transparency and faster vulnerability response, as articulated by Charlie Bell, Executive Vice President, Microsoft Security.
The CVE program recently updated the rules that provide guidance to CVE Numbering Authorities (CNA) like Microsoft. This direction towards greater transparency is encouraged by these new rules. Section 4.2.2.2 states:
4.2.2.2 CNAs SHOULD Publicly Disclose and assign a CVE ID if the Vulnerability:
- has the potential to cause significant harm
or
- requires action or risk assessment by parties other than the CNA or Supplier.
The “or” between items 1 and 2 is significant because it encourages CNAs to assign CVEs to significant vulnerabilities, regardless of customer action. We encourage all CNAs to assess how these new rules affect their products.
MSRC acknowledges that not all customers want to invest time and energy in addressing this new class of CVEs that don’t require further action. As a result, we are updating the Security Update Guide and APIs to filter based on this criteria.
-
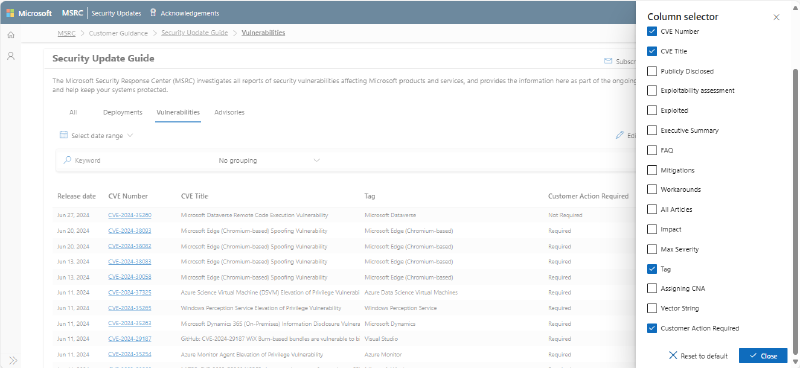
On the Security Update Guide Vulnerabilities tab, there will be a new column to show whether customer action is required.
-
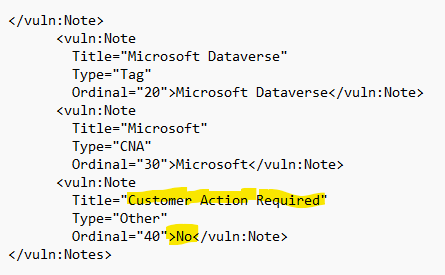
In the API there will be a new Notes Type for the filtering process.
-
In the CVE.org record, we will use the exclusively-hosted-service tag to indicate that there is no action required by the customer.
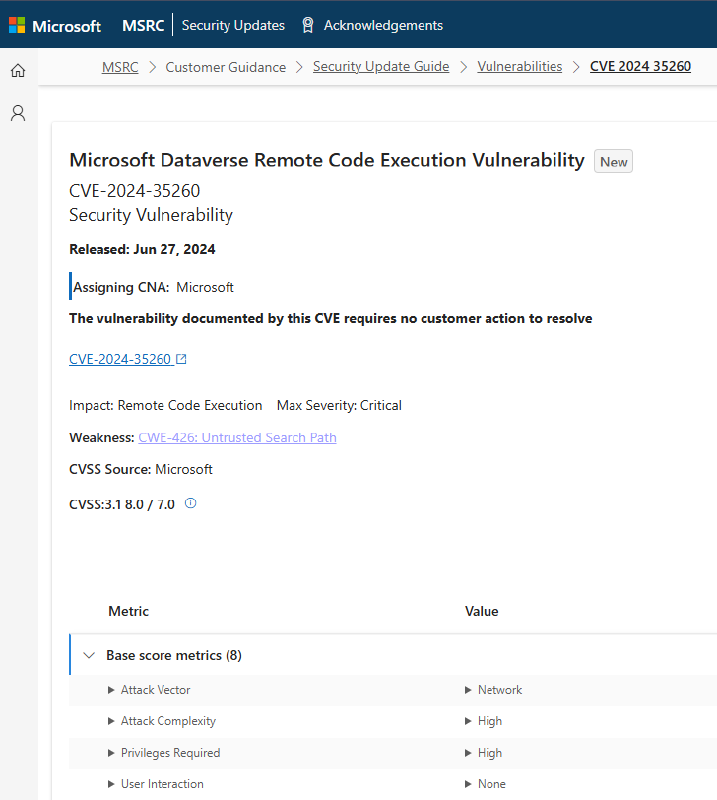
CVE-2024-35260 is an example of this new class of CVEs.
As always, we look forward to your feedback, which you can provide by clicking on the rating banner at the bottom of every CVE page in the Security Update Guide.
Lisa Olson, Senior Program Manager, Security Release