At the Microsoft Security Response Center (MSRC), our mission is to protect our customers, communities, and Microsoft from current and emerging threats to security and privacy. One way we achieve this is by determining the root cause of security vulnerabilities in Microsoft products and services. We use this information to identify vulnerability trends and provide this data to our Product Engineering teams to enable them to systematically understand and eradicate security risks. We also publish these trends publicly to share our learnings and best practices, for example in Pursuing Durably Safe Systems Software.
For decades, we have used our own proprietary taxonomy to describe vulnerability root cause. Today, we are pleased to announce a significant shift: we will now publish root cause data for Microsoft CVEs using the Common Weakness Enumeration (CWE™) industry standard. We believe adopting CWE will better serve our customers, developers, and security practitioners across the industry. This standard will facilitate more effective community discussions about finding and mitigating these weaknesses in existing software and hardware, while also minimizing them in future updates and releases. Ultimately, our commitment to CWE represents a meaningful step toward a more cyber-secure world. This work is core to the goals of Microsoft’s Secure Future Initiative (SFI), outlining our engineering priorities to transforming software development, implementing new identity protections, and improving transparency and faster vulnerability response, as articulated by Charlie Bell, Executive Vice President, Microsoft Security. The CWE is a community-developed list of common software and hardware weaknesses. A “weakness” refers to a condition in a software, firmware, hardware, or service component that, under certain circumstances, could contribute to the introduction of vulnerabilities. Below is an example of Microsoft Windows CVE, including information related to CWE.
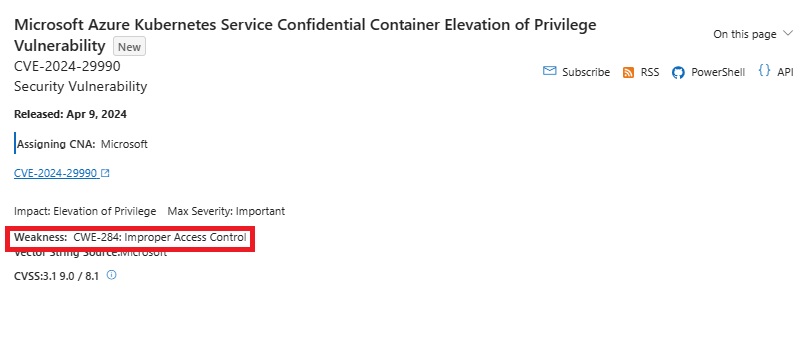 As an industry, we cannot manage what we cannot measure. Providing accurate CWEs for our own vulnerabilities, as well as encouraging our industry peers to do the same, is key to systematically understanding, mitigating, and eliminating whole classes of vulnerabilities. Other industries, such as the medical and transportation sectors, are adept at categorizing and reporting facts, both positive and negative. Our industry and customers will benefit from greater transparency and interoperability through CWE adoption.
As an industry, we cannot manage what we cannot measure. Providing accurate CWEs for our own vulnerabilities, as well as encouraging our industry peers to do the same, is key to systematically understanding, mitigating, and eliminating whole classes of vulnerabilities. Other industries, such as the medical and transportation sectors, are adept at categorizing and reporting facts, both positive and negative. Our industry and customers will benefit from greater transparency and interoperability through CWE adoption.
Additionally, the CWE information provided will not only be displayed in the Microsoft Security Update Guide but will also be available in the SUG CVRF API and instantiated on CVE.org and NVD.nist.gov.
As always, we look forward to your feedback which you can provide by clicking on the rating banner at the bottom of every CVE page in the Security Update Guide.
Lisa Olson, Senior Program Manager, Security Release
