With the launch of the new version of the Security Update Guide, Microsoft is demonstrating its commitment to industry standards by describing the vulnerabilities with the Common Vulnerability Scoring System (CVSS). This is a precise method that describes the vulnerability with attributes such as the attack vector, the complexity of the attack, whether an adversary needs certain privileges, etc. You can find more information about CVSS here and even take a short online course here. The Microsoft Security Response Center has been scoring Windows and Browser vulnerabilities since 2016. Now we are scoring every vulnerability and displaying the details that make up that score in the new version of the Security Update Guide.
Let me show you a comparison between the old and new article and then you can see how moving to this model has benefits:
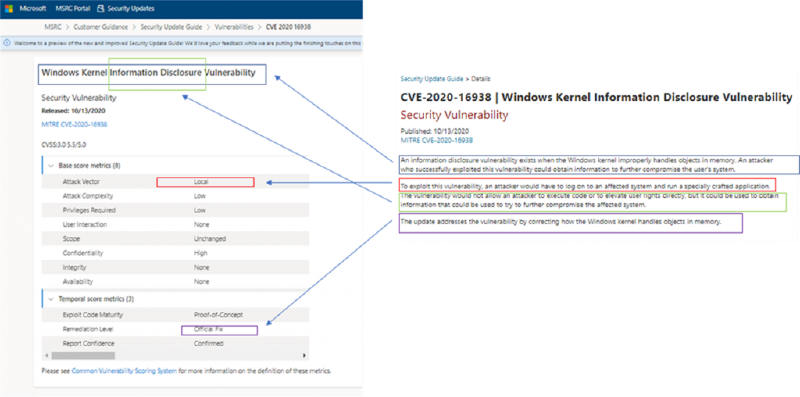
Comparison between the new SUG articles and the previous model
- You can see that the CVE Title “Window Kernel Information Disclosure Vulnerability” is a more succinct form of the first paragraph: “An information disclosure vulnerability exists when the Windows kernel improperly handles objects in memory. An attacker who successfully exploited this vulnerability could obtain information to further compromise the user’s system”
- The second paragraph starts out with: “To exploit this vulnerability, an attacker would have to log on to an affected system and run a specially crafted application”. This is the described in the first element of the CVSS score “Attack Vector”. In this case it is local which is equivalent to “log on to affected system”. The second sentence just reiterates that it is an Information Disclosure.
- The conclusion is that we’ve fixed it “The update addresses the vulnerability by correcting how the Windows kernel handles objects in memory.” This information is also in the CVSS scoring in the Remediation Level element.
So, you see? There wasn’t much to the three paragraph descriptions, though they were comforting. The information in the CVSS score contains all sorts of more useful information. For example, if the scope is Changed , it means that the exploit can start in one place, say application memory, and jump to another place like the kernel memory. If the Scope value in the example above was Changed instead of Unchanged , the score would move from 5.5 to 6.5. So, you can use the score to assess the risk of the vulnerability. You can use the CVSS Calculator to see what effect changing these values does to the base score.
Another example:
Understanding which variables in the SUG reports influence how CVSS scores are calculated
-
Here:
-
We can see that the attack vector is listed as Network which is detailed in paragraph One. SharePoint Server is hosting content on a remote server, and users browse to the SharePoint site.
-
To exploit this vulnerability, the attacker will need permission to upload content to the server. A non-administrator account is capable of uploading content, so Privileges Required is set to Low. Additionally, a targeted user needs to interact with the malicious content once it has been uploaded, hence User Interaction is set to Required. One thing to note is that in paragraph Two, this article didn’t specifically call out the need for a targeted user to interact with the malicious content; however, this is represented in the CVSS score.
-
-
This vulnerability also demonstrates a situation where the Scope would be marked as Changed. The vulnerable condition exists on the SharePoint Server, but the vulnerability results in the exploit affecting any system that browses to the site. The server is unaffected, but the client is impacted!
Fun Facts in the new version of the Security Update Guide
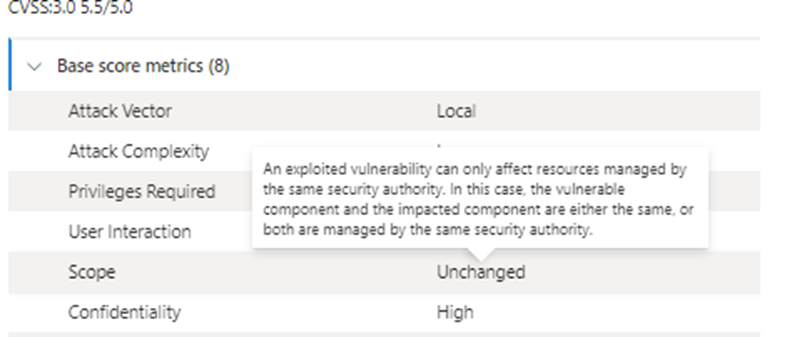
1. You can hover over any of the elements in the score description to see the definition of that element:
Hovering over elements in the score description for a definition of the element
2. For those of you who like to use the API to download the security updates information, you will be happy to know that we’ve updated the scripts in the MSRC-Microsoft-Security-Updates-API Repository on GitHub to reflect the change to the vulnerability descriptions. Here is how you get a report showing a month’s worth of data in a PowerShell environment.
Install-Module MSRCSecurityUpdates-Force Import-Module MSRCSecurityUpdates Set-MSRCApiKey -Verbose -ApiKey "YourAPIKey" $cvrfDoc=Get-MsrcCvrfDocument-ID 2020-Oct $CVRFDoc | Get-MsrcVulnerabilityReportHtml | Out-File -FilePath Oct20.html
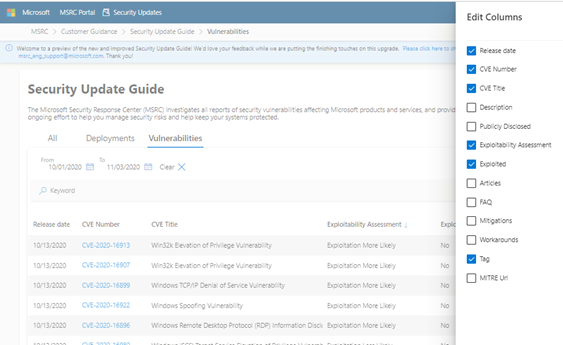
3. The Vulnerabilities tab on the new Security Update Guide shows you a list of CVEs, and you can choose what columns you want to see!
Select all or only the columns you need - the choice is yours!
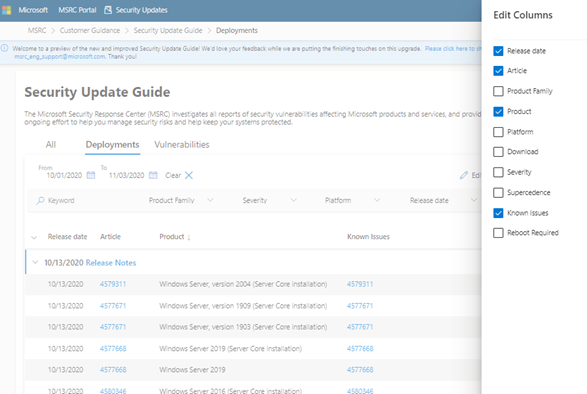
4. You can create a list of KB articles that have Known Issues by using the Edit Column feature on the new Deployments tab.
Customize your KB articles by selecting all or only the columns you need.
5. Did you notice that you can go into Dark Mode?
Enable Dark Mode by clicking on “theme” in the Settings menu (the cog icon).
We hope that you enjoy finding your way around the new Security Update Guide. Please let us know what you think about it here or by emailing us at msrc_eng_support@microsoft.com.
_Lisa Olson, Senior Security Program Manager, _Microsoft Security Response Center